Phishers Used Ukrainian Government Site in Attempt to Target Chase Bank Users

Digital fraudsters launched a phishing attack using a Ukrainian government website in an attempt to steal Chase Bank users’ account credentials.
Inside the Phishing Email
Near the end of September 2020, the Zix | AppRiver team received an email from what at first glance appeared to be Chase Bank.
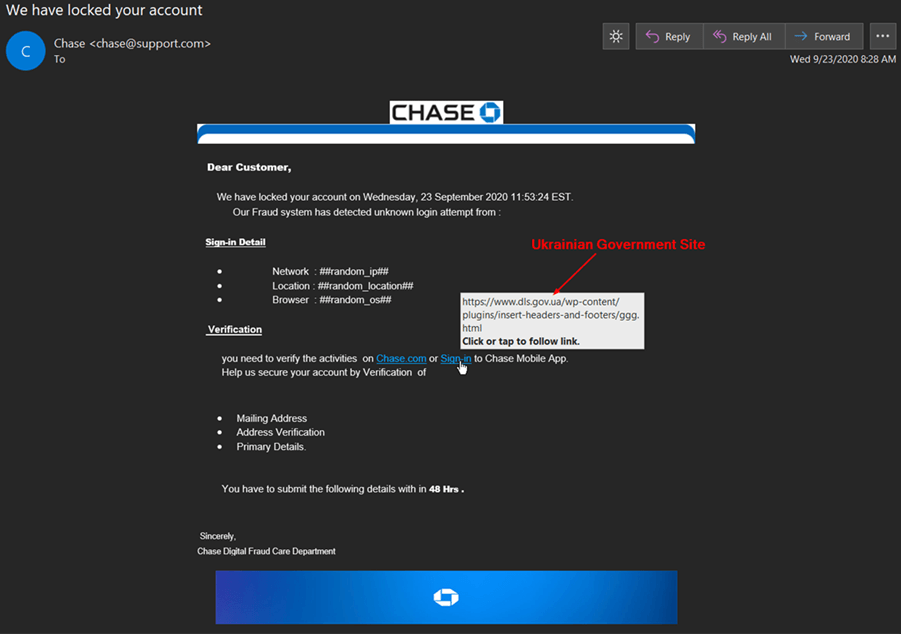
The email stole branding from Chase Bank to try to legitimize the claim they had locked the recipient’s account after detecting an unknown login attempt.
Subsequently, the email instructed the recipient to sign into their account either via the Bank’s website or mobile app so that they could verify the account activities.
Where the Phishing Email Fell Short
The individuals responsible for crafting this phishing email might have thought their malicious activities were clever, but the email was full of holes.
The troubles began even before the recipient got to the actual email message.
Like many phishers before them, these attackers sought to convince the recipient the message had indeed originated from Chase by using spoofing techniques. In the spirit of a support-related email, attackers created an email address that hinted at Chase Bank’s support team. The issue is that they got it backwards: instead of “support@chase.com” or something along those lines, they used “chase@support.com.” Anyone who looked at that address would have realized the email had not come from Chase Bank.
So close, scammers. But not close enough.
Similarly, the fraudsters didn’t proofread their email. The message itself contained all types of capitalization and spacing errors along with some awkwardly worded phrases. Get a whiff of this doozy:
“Help us secure your account by Verification of
- Mailing Address
- Address Verification
- Primary Details.
You have to submit the following details with in 48 Hrs . [sic]”
It’s only fitting the scammers signed off as “Chase Digital Fraud Care Department,” an entity which doesn’t actually exist.
Following the Click
Here’s where things get interesting. The attack email arrived with two embedded links: Chase.com and Sign-in. In the event the recipient hovered over the latter URL, they found that the link’s parent domain was dls.gov.ua. This just happens to be the official website for the government of Ukraine.
Not only that, but the URL seemed to send recipients to a page associated with a WordPress plugin that was active on the website.
Let’s just say that the use of WordPress to host a national government’s website isn’t something that pops up on the radar very often.
Ultimately, clicking on that link led recipients to a fake page disguised as Chase Bank’s login portal, designed to steal visitors’ credentials, and then send them to a server under the attackers’ control.
A closer look of the Ukrainian government website included in this campaign revealed it had an effective URL hosted on demo.primestonemedia[dot]com.
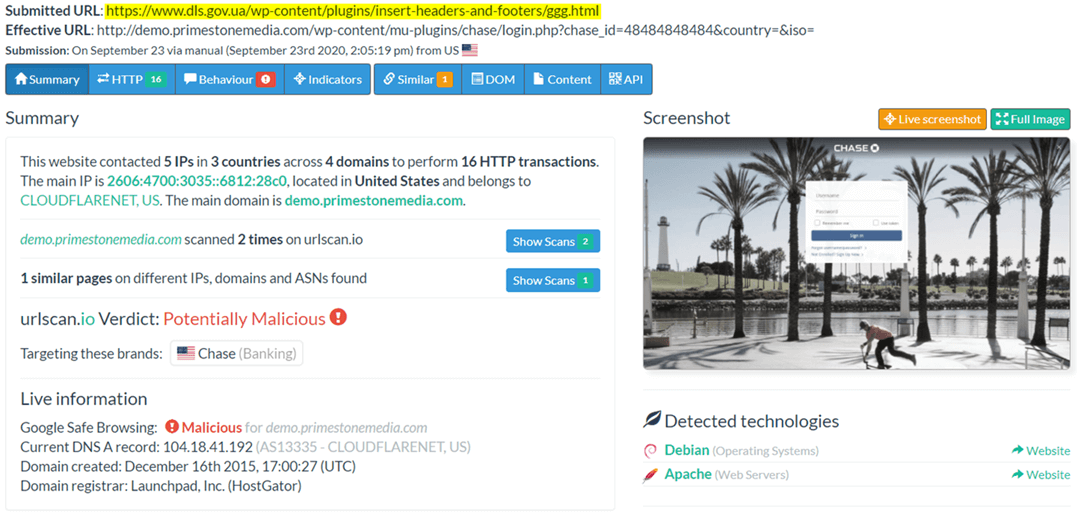
A Google search revealed this domain has a history with Chase Bank phishing scams.
At the time of writing, this phishing page was offline.
Defending Against Chase Bank Phishing Attacks
The attack attempt described above highlights the need for organizations to defend themselves against phishing attacks that impersonate respected entities like Chase Bank. They can do this by investing in a security solution that scans incoming emails for malware signatures, campaign patterns and other indicators of threat behavior. Such analysis should occur in real time, thereby allowing legitimate correspondence to reach their intended destination.
Learn how email threat protection solutions from Zix | AppRiver can help.
