Bank of America Phishing Email Used Numerous Tricks to Prey Upon Recipients

Security researchers detected a phishing campaign whose attack emails employed numerous tricks to steal recipients’ Bank of America (BOA) account credentials.
In the middle of June, security firm Armorblox observed a BOA phishing arrive in a customer’s inbox. The message informed the recipient that BOA was in the process of recycling its customers’ inactive email addresses. In support of this ruse, the attack email instructed the recipient to verify their email address by clicking an “Update email address” button. It warned them that the email address could become available to someone else, thus preventing BOA from sending important account information, in the event the recipient didn’t comply.
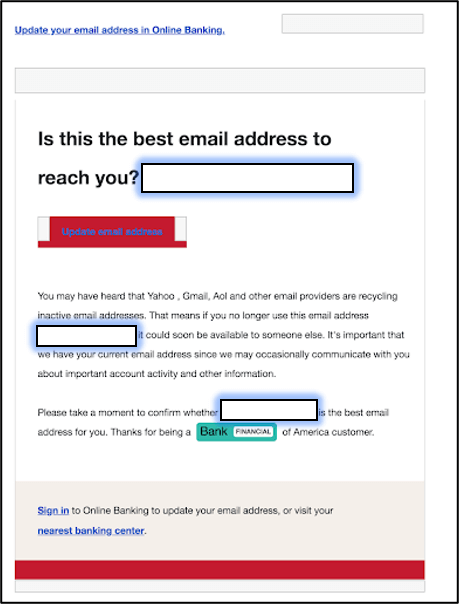
Clicking on the “Update email address” button embedded in the email message redirected the recipient to a phishing site designed to look like the Bank of America official login page.
Who Can Recycle Email Addresses? (Hint: Not BOA)
Before we proceed any further, let’s take a moment to point out just how nonsensical this attack email’s lure really is.
The issue with the phishing campaign above boils down to the fallacy that an entity like Bank of America could recycle users’ email accounts.
Recycling email addresses in general isn’t a new practice. Yahoo is known to have previously recycled email addresses. This didn’t go so well back in 2013 when these email addresses’ new owners were still receiving messages for their previous owners. Some of those emails even contained passwords, according to Naked Security. In response to these issues, Yahoo and Facebook worked together to develop the Require Recipient Valid Since (RRVS) email security protocol, as Techlicious reported at the time.
But recycling email addresses makes a lot more sense for Yahoo because the organization is an internet service provider (ISP) that enables users to obtain a free email account. It directly deals with email services for users. As such, it’s in a position to interact with and/or recycle inactive email addresses if it so chooses.
The same cannot be said for the Bank of America. As a financial institution, BOA has the authority to ask that users update their emails and/or contact information. But it has no control to transfer an email address from one user to another.
Armorblox noted that digital attackers had designed the attack emails specifically to trick users into overlooking that point. As its researchers noted in a blog post:
The sender name impersonated Bank of America, making the email likely to get past eye tests when people glanced through it amidst hundreds of other emails in their overflowing mailboxes. The email language and topic was intended to induce urgency in the reader owing to its financial nature. Asking readers to update the email account for their bank lest it get recycled is a powerful motivator for anyone to click on the URL and follow through.
How the Attack Emails Got Through
The phishing emails described above made their way past email security controls for several reasons identified by Armorblox in its research. These included the following:
- The phishing campaign did not prey upon a targeted organization’s employees indiscriminately. Instead, it directed its attack emails at just a fraction of employees, thereby diminishing the risk of the emails getting caught in bulk email filters.
- Notwithstanding the spoofing techniques in place, the attack emails originated from a personal Yahoo account via SendGrid. This tactic helped the emails to bypass authentication checks such as DMARC.
- Those responsible for the operation created a new domain for their nefarious efforts. In so doing, they ensured that the emails would bypass filters designed to spot known bad links. More than that, they used social engineering techniques to create a lookalike website hosted at “nulledco[.]store,” a non-BOA domain. Malicious actors presumably created this domain for the purpose of launching their attack campaign on June 1.
- Upon receiving a set of login credentials, the phishing website asked the victim to complete three security questions. This behavior mimicked the security mechanisms employed by the Bank of America’s legitimate website. Assuming the victim submitted this information, the attackers could have then leveraged that stolen information to conduct identity theft.
Not the Only BOA-Themed Phishing Email Recently Discovered
The attack campaign described above wasn’t the first operation in which malicious actors sent out phishing emails that abused Bank of America as a lure. Back in the middle of June 2020, for instance, Zix | AppRiver came across an attack email not dissimilar from the one described above. Via the use of spoofing tactics and social engineering techniques, that message claimed that Bank of America could not verify the recipient’s account information. It then instructed the recipient to confirm their contact information by clicking on a “Sign In” button and authenticating themselves.

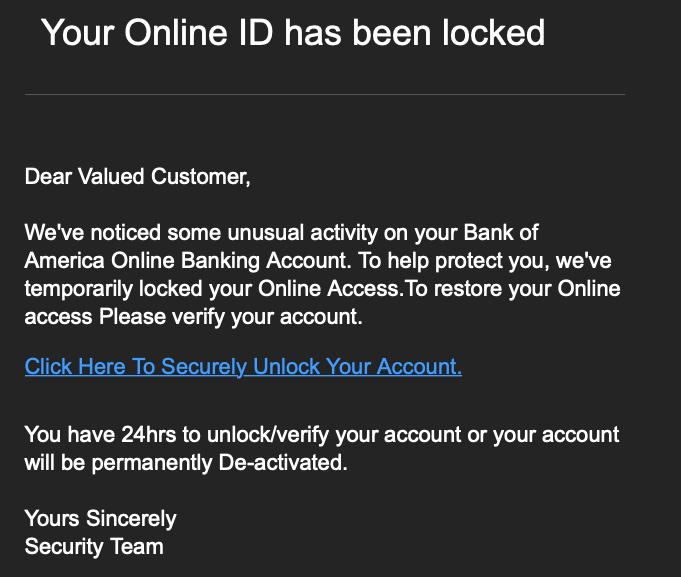
Not every BOA-themed phishing email spotted in the wild has stolen the Bank of America’s branding to come across as legitimate. Indeed, Zix | AppRiver also came across a more “subtle” email attack operation that lacked BOA’s logo. (The email message did use spoofing techniques to create the appearance that it came from the Bank of America, though. It also mentioned the financial institution several times in its body text.) Using the claim that BOA had detected unusual activity, the attackers used their email to pressure the recipient into verifying their account by clicking on a “Click Here To Securely Unlock Your Account.” The email warned that recipients would lose access to their accounts within 24 hours unless they verified themselves.
The Zix | AppRiver team came across one more BOA-themed phishing email in recent weeks. Arriving only with the subject line “Important Message,” the attack email informed the recipient that they needed to reconfirm their email address and mobile phone number in order to continue to process money transfers. The email also sought to assuage the recipient’s concerns by informing them how they could verify the message’s legitimacy:
Want to confirm this email is from Bank of America? Sign in to Online Banking and go to Alerts. The Alerts History lists the Alerts sent to you in the past 60 days. To verify that this email is from Bank of America, confirm your last sign-in date is correct. To access Online or Mobile Banking, go directly to bankofamerica.com or use our Mobile Banking App.
The email included an “update contact information” link. Recipients who clicked on the link found themselves redirected to website designed to look like the Bank of America login page. That website concealed a phishing kit designed to steal a recipient’s credentials.

How to Defend Against Phishing Attacks
Organizations can defend themselves against phishing attacks such as those described above by investing in their email security. They can do this by deploying a tool that’s capable of scanning incoming messages for signs of known threat behavior. This solution should perform these analyses while allowing legitimate correspondence to reach their intended destination.
Learn how Zix | AppRiver can help organizations strengthen their email security defenses.
