Snake Campaign Used Executable File Packed with Dinosaur Game

Malicious actors packed a dinosaur game into an executable file as part of their efforts to distribute the Snake keylogger.
Breaking Down the Attack Email
In the middle of March, the Zix | AppRiver team detected one of the campaign’s attack emails.
The message arrived with the subject line “RE: PAYMENT INSTRUCTIONS,” and it appeared to have originated from administrative personnel working within an unnamed organization’s “Accounts Department.”
Using those features as camouflage, those responsible for this campaign informed the recipient that they had twice attempted to wire payment to their account for an unspecified good or service but had encountered issues along the way. They went on to instruct the recipient to open an attached set of instructions to ensure that they could receive payment this time around.
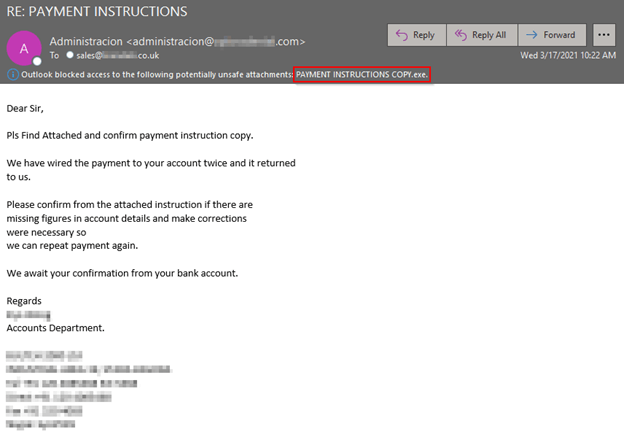
Screenshot of the attack email. (Source: Zix | AppRiver)
It’s clear from the screenshot above that the attack email was a fake. The grammar mistakes and awkward phrasings were the first giveaway that something was off. As an example, whoever crafted the email started their message with the formal salutation “Dear Sir” but then abbreviated “Please” and for some reason capitalized “Find Attached” in the first sentence.
There was also this beauty of a sentence in the third paragraph:
“Please confirm from the attached instruction if there are missing figures in account details and make corrections were necessary so we can repeat payment again.”
Second, the attackers didn’t send along the “payment instructions” in a familiar document type that the recipient might have expected. A Word document or Excel spreadsheet would have made sense, for instance. But who sends along payment instructions in an executable file?
It’s therefore no surprise that this file contained Snake. According to Malwarebytes, Snake is a piece of Russian-made malware that’s been infecting Windows systems since at least 2008. Fox-IT discovered a macOS variant of the threat, otherwise known as the “404 Keylogger,” nearly a decade later. Just a few years after that, Lastline spotted attackers using COVID-19 as a lure to spread Snake and other well-known infostealers.
The Surprise of This Payment Instruction Malware Campaign
Troy Gill, manager of security research, analyzed the executable file attached to the campaign’s attack email. He found a surprise in the process.
“The malicious actors packed a dinosaur game into this executable file,” he told me in an email. “There are also references in here to ‘TRexUI.’ This could potentially be Google Chrome’s offline dinosaur game. This is a relatively common tactic to pack legitimate programs like games into malicious executables to try and evade detection.”

Screenshot of the executable file. (Source: Zix | AppRiver)
Gill also said that he didn’t believe the attacks he was observing as part of this campaign were associated with state-sponsored activity. He said that the variant was most likely one that had been repurposed by a digital crime group and sold on an underground web marketplace.
How to Defend Against an Evasive Snake Campaign
The attack email discussed above highlights the need for organizations to strengthen their security posture against email attacks carrying well-known keyloggers. One of the ways they can do that is by investing in a security solution that’s capable of scanning incoming emails for malware signatures, campaign patterns, IP addresses and other indicators of known threat behavior. This tool should come with the capability to perform this analysis in real time so that legitimate business correspondence can reach its intended destination in the organization.
